Hacking
18 Stories

Hacker Claims Data Breach at HPE, Prompting Investigation
Hacker Steals Sensitive HPE Data: Hewlett Packard Enterprise (HPE) is under inquiry after claims by a hacker, operating under a...

Russian Hackers Target WhatsApp Accounts of Ministers Worldwide
Reports of Russia allegedly attempting to hack the whatsapp accounts that belong to government ministers and top-ranking officials across the...

Your data might already be breached
If you think hackers aren’t trying to infiltrate your business or organization, you are probably lying to yourself. The average...

Is your password secure?
We all know the old rule of never recycling passwords, but how many of us actually follow this advice? In...

5 lessons from recent data breaches
Technology has revolutionized the way we do everything, including shopping. Now instead of having to go to the store and...
![Preventing ATM Theft [Infographic]](https://staging.techi.com/wp-content/uploads/2014/09/6134-close-up-of-three-credit-cards-or-a-264x176.jpg)
Preventing ATM Theft [Infographic]
Every year, ATM skimming costs America $8.5 billion, most of which is paid by consumers and institutions. Skimming accounts for...

Your data is at risk: 5 eays to protect it
Heartbleed made the rounds in the media as the security threat du jour. What made Heartbleed so dangerous was that...

First “Heartbleed Attack” makes wave
In the past couple of weeks you’ve probably received emails, Facebook posts, or tweets warning about the Heartbleed virus, but...

Your smartphone could be hacking your life
The smartphone is a tricky device and sometimes the lines between master and servant are blurred. On one hand we...
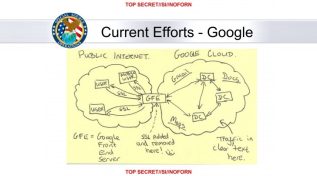
Why the NSA tapping of Google and Yahoo clouds is more dangerous than PRISM
Could we be getting "NSA fatigue"? No, I'm not talking about the obvious weariness that we have about the National...

Where is your POS system vulnerable?
When it comes to point-of-sale, there are a few vulnerabilities that you probably didn't even know were there. In 2012, the...

Tips to protect your social media accounts
There are a few risks that come with social media. Few of them are very serious, but it is always...
Page 1 of 2